Quantity vs quality
Today, Apple puts Touch ID sensors in almost all devices (with the exception of the iPod Touch line), while manufacturers of Android smartphones were able to access the required API only with the release of Android 6.0, which now runs about 15% of devices. Let's try to figure out how safe the fingerprint authentication method is and whether its use makes practical sense.
Following the historical order, we will begin, perhaps, with Apple.
Collecting unprotected images
Image Credit: tarik_vision/DepositPhotos
If a hacker captures your fingerprint image, they hold the key to breaking into your scanners. People can change the password, but the fingerprint remains the same for life. This consistency makes them a valuable tool for hackers who want to get past the fingerprint scanner.
Unless you're very famous or influential, it's unlikely that a hacker will dust everything you touch to get their fingerprints. Most likely, a hacker will target your devices or scanners in the hope that it contains your raw fingerprint data.
For the scanner to identify you, it needs a basic image of your fingerprint. During setup, you provide your fingerprint to the scanner and it stores an image of it in its memory. It then calls up this image every time you use the scanner to ensure that the finger scanned matches the one you specified during setup.
Unfortunately, some devices or scanners store this image without encryption. If a hacker gains access to the storage, he can easily capture the image and collect your fingerprint data.
How to avoid this attack
To avoid these types of attacks, you need to consider the security of the device you are using. A well-made fingerprint scanner should encrypt the image file to prevent prying eyes from getting your biometric data.
Double check your fingerprint scanner to make sure it stores your fingerprint images correctly. If you find that your device does not resolve to securely store your fingerprint image, you should stop using it immediately. You should also look into deleting the image file to prevent hackers from copying it for themselves.
Touch ID and Secure Enclave: a sweet couple
Three years ago, the problem with Apple, which was already beginning to pay attention to data security at that time, was that users for the most part did not want to protect their own devices in any way. Enter a PIN code to unlock your phone? It's long and inconvenient. After looking at the situation, Apple decided not to force people to use lock codes, but simply to simplify the unlocking process as much as possible. The main idea of Touch ID technology is not to make your specific device safer. The idea is to make security convenient and attractive enough for the majority of users. And the company achieved its goal.
Touch ID is a unique software and hardware complex, and the word “unique” here does not carry an advertising connotation: each sensor during the production process is configured to work with a specific device. Remember the “error 53” scandal? It was this feature that became a stumbling block that blocked the operation of devices with a fingerprint sensor replaced in makeshift conditions.
Setting up face unlock for Samsung Galaxy A51 smartphone
It is better to register your face indoors so that your face is not exposed to direct sunlight.
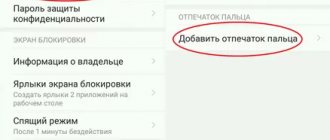
1 On the Settings screen, tap Biometrics & security → Face recognition. 2 Read the onscreen instructions and select Continue . 3 Set the screen lock method. 4 Select whether you wear glasses or not, and then select Continue . 5 Turn your device so that the screen is facing you and look directly at the screen. 6 Position your face inside the frame on the screen. The camera will scan your face.
✓ If unlocking the screen using face recognition does not work, select Delete face data to delete the registered data and try again. ✓ To improve the quality of face recognition, select Alternative Appearance and add an alternative appearance.
Deleting a registered person's data
The registered person's data can be deleted.
1 On the Settings screen, tap Biometrics & security → Face recognition . 2 Unlock the screen using your selected screen lock method. 3 Select Delete face data → Delete . Once a registered person's data is deleted, all related functions are also disabled.
Face unlocking
You can unlock the screen with your face instead of using a pattern, PIN, or password.
1 On the Settings screen, tap Biometrics & security → Face recognition. 2 Unlock the screen using your selected screen lock method. 3 Tap the Face unlock to turn it on.
✓ To set your device to unlock the screen without swiping on the locked screen after recognizing your face, tap the Stay on lock screen toggle to disable the feature. ✓ If you want to reduce the likelihood of faces being recognized in photos or videos, tap the Accelerated recognition to enable the feature. Face recognition speed may be reduced. ✓ To improve recognition speed in low light conditions, tap the Increase screen brightness to turn on the corresponding function.
4 Look at the locked screen to unlock it. When the face is recognized, the screen will unlock without any additional procedures. If your face is not recognized, use the preset screen unlock method.
Read in full: Instructions for using the Samsung Galaxy A51 mobile phone. Reboot, update...
Where are fingerprints stored?
It would seem that the need to store fingerprint data in the form of a one-way hash function is obvious, but it only seems so to you: the developers of HTC One Max decided that they can store fingerprints in the form of pictures in the most ordinary folder in the device’s memory. Whatever the HTC developers thought, Apple engineers did not make such a mistake: the scanned fingerprint is passed through a hash function and stored in the Secure Enclave, a microcomputer protected from outside access. Separately, I note that this data does not go to iCloud and is not transferred to the company’s server.
Interestingly, even the one-way fingerprint hashes are encrypted, with encryption keys calculated at device boot time based on a unique hardware key (which is also stored inside the Secure Enclave and cannot be retrieved from there) and a lock code that the user enters. Decrypted fingerprint data is stored only in the device's RAM and is never saved to disk. At the same time, the system from time to time deletes fingerprint data even from the device’s RAM, forcing the user to log in using a lock code (which, we recall, will allow the system to decrypt the fingerprint data and resume the operation of the Touch ID sensor).
When and why iOS deletes fingerprint data from RAM
Perhaps the most interesting thing about iOS security is the question of under what circumstances iOS will delete fingerprint data from the device’s RAM and force the user to re-authorize using an unlock code. But first, let's think about why Apple even needed to periodically delete fingerprints?
The company understands very well (and understood three years ago) that any biometric system can be deceived. Yes, Apple has developed excellent fingerprint scanners, which are not as easy to bypass as a sensor on, for example, the Samsung Galaxy S5. But it’s still possible. After all, the owner can be forced to use their finger to unlock the phone - only under the American legal system, this requires a warrant, which takes time to obtain... after which the phone will erase the fingerprint data from its memory and will not allow the device to be unlocked with a fingerprint.
Sounds like a stretch? Smacks of a conspiracy theory? No, Apple just really didn’t like the attempt at pressure from law enforcement agencies, in response to which it introduced this measure: Apple adds another rule forcing iPhone and iPad users to employ a passcode to unlock their device.
But let’s not get distracted, but look carefully at the conditions under which the system blocks Touch ID and forces you to log in using a lock code. The Touch ID sensor is turned off and fingerprint data is cleared from the device memory when any of the following conditions are true:
- the phone is turned off or rebooted;
- the user adds the data of another finger;
- the phone receives a remote lock command via Find My iPhone;
- there were five unsuccessful attempts to unlock using a fingerprint in a row; • the device was never unlocked for two days;
- anti-policeman: more than six days have passed since the last time the lock code was entered, and the device itself has not been unlocked by the Touch ID sensor within the last eight hours.
The meaning of the last point needs to be clarified. According to the PhoneArena website, it “may complicate the work of law enforcement agencies.” I would put it more confidently, because the last point was introduced immediately after the sensational trial with the terrorist from San Bernardino, when unprecedented pressure was put on Apple.
Samsung Galaxy A50 smartphone lock screen
To turn off and lock the screen, press the Side key. Additionally, the screen automatically turns off and locks if the device is not used for a certain period of time.
To unlock the screen, swipe in any direction on the turned on screen.
When the screen is off, press the side key to turn on the screen. You can also double-tap the screen.
Changing the screen lock method
To change the screen lock method, launch the Settings , tap Lock screen → Screen lock type , and then select a lock method.
By setting a pattern, PIN, password, or your biometrics for the screen lock method, you can protect your personal data so that others cannot access it. Once you set the screen lock method, you will need an unlock code to unlock your device.
• Swipe : Swipe the screen in any direction to unlock. • Pattern : Create a pattern of at least four dots to unlock the screen. • PIN : Enter a PIN of at least four digits to unlock the screen. • Password : Enter a password of at least four numbers or symbols to unlock the screen. • None : Without setting a screen lock method. • Face : Register a face to unlock the screen. • Fingerprints : Register your fingerprints to unlock the screen.
If you enter the wrong unlock code several times in a row and reach the limit on the number of attempts, the device will reset to factory settings. Open the Settings , tap Lock screen → Security lock settings , unlock the screen using your screen lock method, and then tap the Auto reset to turn it on.
Read in full: Samsung Galaxy A50 smartphone - description, reset...
How to bypass the fingerprint scanner
If we are talking about hacking Touch ID, then it is difficult to deceive the sensor, but it is possible. To fool modern sensors, you will have to create a three-dimensional model of your finger, and from the right material. On older devices (iPhone 5s, iPad mini 3), bypassing the sensor is much easier. For example, a team of German hackers was able to scan the iPhone 5s sensor two days after the device went on the market by simply printing the original fingerprint at 2400 dpi.
But before you start simulating a fingerprint, you need to take care of the safety of the data on the device, and also that the fingerprint data does not have time to “rotate”.
You need to act clearly and quickly: you have a minimum of time.
- So, a phone in an unknown state fell into your hands. Don't touch the Touch ID button! If your phone is locked (and it most likely is locked), you'll waste one out of five attempts. Check the device status by briefly pressing the power button.
- If the device is blocked, isolate it from external radio networks by placing it in a Faraday cage (at home, a regular microwave will perform its role. The microwave is turned off!). Don’t forget to put it on charge, even if its role is played by an external battery. All this is done in order to protect the device from commands via the Find My iPhone protocol, which will allow you to both remotely lock the device and destroy its contents. (Do you think these measures are obvious? No matter how they are! Science knows of at least two high-profile cases where police allowed the remote destruction of data from already confiscated devices.)
- But if the device is unlocked, it is up to you to prevent it from locking the screen. To do this, simply disable automatic locking (unlike the procedure for removing the locking code, you do not need to enter any code to disable automatic locking).
- If the device has been locked, you have a maximum of 48 hours (actually less) to try to fool the fingerprint sensor.
- Please note: all manipulations with the device must be carried out exclusively in an environment protected from radio waves (Wi-Fi networks and cellular networks). It only takes a couple of seconds for Find My iPhone to work.
- If you managed to fool the fingerprint sensor, disable automatic screen locking (see point 3). Keep in mind: attempts to add another fingerprint in the settings or change the lock code will not work - for these operations the system will always require you to enter a code.
How to use it?
Let's say you managed to fool the fingerprint sensor. What's next? iOS is a closed system, and all device memory will be encrypted. Options?
- Jailbreak installation: no. To hack a 64-bit iPhone or iPad, you will in any case need to enter the lock code (and in some cases, also disable the lock code in the settings).
- Physical data extraction: you can try. If you are already jailbroken, you will be able to extract most of the data, but you will not be able to decrypt the keychain. But if there is no jailbreak, then nothing can be done - to install it you will need a lock code.
- iCloud: possible. Once you unlock your device, you can force it to save a fresh backup to iCloud (Settings –> iCloud –> Backup –> Backup now). Remember, however, that to retrieve this data from the cloud, you will need your Apple ID password, and if two-factor authentication is activated on your account, then access to the second factor (which, however, can be the device under study). An important point: you will have to connect the device to Wi-Fi, as a result of which, instead of a backup copy, a command to block or destroy data may arrive on the device.
- iTunes backup: perhaps this is the only thing that can and should be done. The unlocked device easily connects to iTunes, which creates a backup copy of the data on your computer. What happens next is a matter of technique. One thing: the password for the backup. If it is installed, you will have to hack it (for example, using Elcomsoft Phone Breaker). But if it is not installed, be sure to install yours! The simplest 123 will be enough. From a backup encrypted with a password, you can extract all the data, and from an unencrypted one, everything except the keychain. Since the keychain stores all the interesting stuff, setting a temporary password before taking a backup will be very useful.
How to unlock Xiaomi Redmi 8 Pro smartphone
Method 1 - password recovery via Google account 1 On the lock screen you must enter the wrong password 5 times in a row, the message “Forgot your password?” 2 By clicking on the inscription that appears in the next window, we see “enter user login” and password for your Google account, of course, the device must be linked to your Google account. 3 The system will prompt you to change your smartphone password. 4 Enter a new password, repeat it and write it down or save it in your memory so as not to repeat the recovery procedure.
Method 2 - restoring access using Xiaomi's own software 1 Go to your PC and go to the company's official website. 2 Download and install the Mi Unlock program on your computer. 3 Connect your smartphone via USB cable. 4 Log in to your Mi account. 5 Turn off the device by holding down the power button simultaneously with the volume down key and enter Fastboot mode. 6 Connect the device to the computer again and click “Unlock”.
Method 3 - system reset (Hard Reset) This will completely reset all phone settings, delete all third-party applications and files, and all your contacts will disappear. Press the power button at the same time as the volume up key. Hold for more than 10 seconds until the smartphone vibrates specifically, release the keys. The phone will load the settings menu, where you need to select Recovery and then Wipe data . The smartphone will reboot and clear all data on the device, remove all previously set passwords and pattern keys.
Method 4 - deleting protective files 1 You need to go to the Recovery menu and select Advanced and then File Manager. 2 You have entered the file system of the phone, where you need to select the Data-system item and delete 5 files that are responsible for the locking passwords of the smartphone itself “gesture.key, password.key, locksettings.db, locksettings.db-wal and locksettings.db- shm." 3 Reboot your device and the job is done, all passwords are removed from the smartphone, it starts in normal mode. And the lock screen will no longer bother you.
Method 5 - Through the smartphone search function 1 Using a PC, go to the official phone search site from Google. 2 Log in and wait for the site to determine the location of your phone. 3 After determining the location of the smartphone, click on the “Erase data” item.
Read in full: How to use the Xiaomi Redmi 8 Pro smartphone.
How to unblock, how to distribute the Internet...
Google Android 4.x–5.1.1: everything is very sad
The first devices with built-in fingerprint sensors began to appear quite a long time ago, back in the days of Android 4.4. Today there are already a lot of them: these are Samsung Galaxy S5, S6, S7, Motorola Moto Z, Sony Xperia Z5, LG G5, Huawei Ascend Mate 7 and subsequent ones, Meizu Pro 5 - and that’s not all. But not every device uses the fingerprint sensor in the correct way. This is primarily due to the fact that until Android 6.0 there was no universal API for fingerprint authentication in the system. No API means no formal Compatibility Definition requirements, and, accordingly, no certification from Google.
In the complete absence of external control, the manufacturers have piled up something like this... you wouldn’t even dream of it in a nightmare. For example, the developers of HTC One Max took an external exam in the “Android in 21 days” course and implemented a wonderful system that stores full copies of fingerprints in a publicly accessible directory in an uncompressed (not to mention encrypted) format. There is probably no need for instructions on how to “hack” this system. Let me just clarify that the data is stored in the file /data/dbgraw.bmp, and for your convenience, the access permission is set to 0666.
This is not an isolated example. Samsung Galaxy S5 came out with Android 4.4 on board. Soon, hackers managed to gain access to the fingerprint scanner and successfully bypass the protection.
Before the release of the sixth version of Android, manufacturers managed to release a ton of devices to which they had incorrectly attached fingerprint sensors. It’s not even interesting to break them, everything is so sad there. It is clear that Google could not tolerate this situation for long. They didn't.
More complex methods
Those who do not want to be a simple user of a mobile gadget, but want to learn how the Android operating system works, may find it useful to use more complex methods of bypassing the lock on their own or someone else’s phone. They will allow you to avoid problems when gaining access to functionality, and in an unusual way.
Unreliable Wi-Fi
Few people know, but you can intercept a password or PIN code via a Wi-Fi network. Former technical director Adrian Collier spoke about this. The technology is called “WindTalker” and is based on network signal analysis.
During the research, it was found that at the moment of entering the password, there is active movement of the fingers across the screen. This creates unique interference and affects the Wi-Fi signal. If the fraudster can create an access point in time, he will be able to track wave oscillations and obtain information about the state of the channel.
For these purposes, a special application with the same name was developed. The algorithm of actions is as follows:
- A public Wi-Fi hotspot is installed in a location that the subject of interest regularly visits and stays for a long time.
- The moment you connect to the network, the program starts and begins tracking its traffic. The hacker becomes an intermediate link between the client and the server
- The application detects the moment in time when the subject is about to enter a password and begins sending requests to his smartphone (at a speed of at least 800 packets per second).
- The device instantly sends echo replies, which are recorded in WindTalker.
- At the end of the session, which lasts milliseconds, the application analyzes the received data and issues a PIN code. Depending on the complexity of the combination, it can have from one to several dozen options.
Another option to obtain the password, which is considered more common today, is to track the data packet using hacking software. If, when connecting to an unsecured Wi-Fi network, a user enters logins and passwords, they can easily “leak” to a hacker.
Fitness trackers
An equally original way to find out the password for accessing a smartphone and even a bank account is to analyze data received from smart watches or fitness bracelets. Employees of the Stevens Institute of Technology and Binghamton University in the USA have developed a unique scanner that is capable of detecting electromagnetic radiation emanating from the sensors of smart watches and fitness trackers.
The device can be installed next to an ATM, terminal, or simply a person’s workplace, and track the movement of his hands. Information from the scanner is transmitted via Bluetooth to an application created for this purpose, capable of detecting up to 5 thousand key movements. If the password is entered once, the scanner recognizes and issues the correct combination with 80% accuracy. In the case where the PIN code is entered twice, this figure increases to 90%.
During the experiment, it was proven that the more sensors (magnetometers, gyroscopes, accelerometers) are present in a wearable device, the higher the accuracy indicators. In this case, the position of the hand does not have any effect on these parameters.
Thermal radiation
It is quite easy to read the password entered from the smartphone screen, armed with a compact thermal imager. During the experiment, which was carried out jointly by scientists from the Universities of Munich and Stuttgart, it was possible to recognize a four-digit code already 15 seconds after input, and a more complex combination - after 30 seconds. Moreover, the correct PIN code was recognized in 90% of cases. To scan the code, just hide the device in your sleeve or disguise it as a toy.
If you suspect influence from a third-party device, the smartphone owner has the opportunity to protect himself from its influence. To do this, experts advise:
- change the brightness of the display, increasing it for a few seconds;
- use random swipes across the screen;
- dramatically load the processor.
Flashing
Typically, flashing is used to solve critical problems in the operating system of a mobile device, but in some cases it is used to bypass device locking. Flashing the firmware is not difficult - to do this, you need to download a specific file that updates the operating system and run it on the phone.
Before starting the process, the user must remember that he will lose the support of the manufacturer, and in case of failure during the update, he may cause irreparable damage to the phone, as a result of which it will be irretrievably lost. In simple words, it will turn into a “brick”.
To avoid possible problems, it is recommended to use only proven products. This means that you should download the installation file only from the official website class=”aligncenter” width=”956″ height=”597″[/img]
Manufacturer service
For the convenience of customers, the largest manufacturers of digital technology have created and are improving proprietary services for unlocking smartphones remotely. Thanks to this, access to the functionality of gadgets can be obtained in just a couple of clicks.
Samsung
To bypass the protection in a Samsung phone, you will need to visit the manufacturer’s official website, create an account and link it to your device. If you need to unlock it, you will need:
- Login to your account;
- In the “Content” section, find the name of your device;
- Activate the screen unlock function by pressing the button of the same name.
Sony
You can access the functionality of the Sony Xperia device in a slightly different way. To do this you will need:
- Download the PC Suite proprietary shell to your PC;
- Using a USB cable, connect your smartphone to your computer;
Launch the program and go to the “Tools” section;- Here, start the process using the “Data Recovery” button.
Follow the prompts on the monitor to open access to the contents of the gadget.
Android 6.0: Fingerprint API and Nexus Imprint
With the release of Android 6.0, Google not only developed its own API for fingerprint authentication, but also updated the Compatibility Definition Document, which all manufacturers who want to certify their devices to install Google services must follow (this is a very important point, more on it later).
Two reference devices were released at once: Nexus 5X and Nexus 6P. They include unbreakable encryption of the data section and the correct implementation of fingerprint sensors, called Nexus Imprint.
So, what does Google require from manufacturers to obtain a certificate of conformity? Unlike the situation with mandatory encryption on Android 5.0, this time the list of requirements does not allow for double interpretation. Let's translate an excerpt from the official document.
Phone hacking apps
You can find a lot of spyware on the Internet, but most of them are ineffective or contain viruses. Therefore, choosing a suitable application should be approached responsibly. Today, the following three programs are popular.
| Application | Description |
| Cocospy | A legal program that does not require superuser rights. The functionality allows you to perform actions such as bypassing the blocking, as well as monitoring SMS, calls, social network profiles, and phone location. |
| mSpy | The second most popular application that allows you to track calls, photos, personal data and other contents of your phone. |
| Spyzie | The program is suitable for those who want to know not only the information contained on the phone, but also that which has already been deleted, primarily for parents. The application is convenient to operate from any gadget. |
7.3.10. Fingerprint sensor
For devices that support a screen lock, the use of a fingerprint sensor is RECOMMENDED. Requirements for devices equipped with such a sensor and providing access to the API to third-party developers:
- You MUST declare support for android.hardware.fingerprint.
- A complete implementation of the fingerprint API from the Android SDK documentation is MANDATORY [Resources, 95].
- MUST have a false positive rate of less than 0.002%.
- False negative rate less than 10%, response latency less than 1 second (for 1 stored fingerprint) is STRONGLY RECOMMENDED.
- It is MANDATORY to limit the speed of attempts to a 30 second delay after 5 unsuccessful attempts.
- It is MANDATORY to have hardware secure storage, and fingerprint verification must be carried out exclusively in the Trusted Execution Environment (TEE) zone or on a dedicated processor with a secure communication channel with the TEE. (This caused a fire on the Samsung S5, which had a problem with the secure communication channel)
- Fingerprint data MUST be encrypted so that it cannot be accessed outside of the Trusted Execution Environment (TEE) according to the Android Open Source Project [Resources, 96].
- MUST not allow adding fingerprints without establishing a trusted chain (user must add or verify PIN/pattern/password via TEE according to Android Open Source).
- DO NOT ALLOW third party applications to distinguish between individual fingerprints.
- It is MANDATORY to process the DevicePolicyManager.KEYGUARD_DISABLE_FINGERPRINT flag correctly.
- ALL OF THE ABOVE REQUIREMENTS ARE MANDATORY when upgrading to Android 6.0, and fingerprint data must either be securely migrated or reset.
- It is PREFERABLE to use the Android Fingerprint icon from the Android Open Source Project.
As you can see, the document does not imply double interpretations. Manufacturers wishing to certify devices running Android 6.0 and above with fingerprint sensors must fully comply with all requirements. Moreover: devices that are updated to Android 6.0 are also required to meet the new requirements (and, accordingly, undergo certification).
Another part of the document requires that encryption be enabled when using a secure screen lock (including a fingerprint sensor). As you can see, in theory things are going well. But what really?
Android Smart Lock
But in fact, Android still has a number of gaping security holes that allow you not just to bypass, but to bypass all these fingerprints and passwords in one go. One of these holes is the Android Smart Lock system, with which you can automatically unlock your phone when certain external factors coincide. For example, many users allow automatic unlocking of the house, forgetting that the positioning accuracy is far from ideal and the concept of “home” for the phone will cover an 80-meter radius. Many activate unlocking with a trusted Bluetooth device or enable pseudo-biometric unlocking using a face photo (this can be done quite easily by showing a video or a 3D model).
Interestingly, there is no need for Smart Lock if there is a working fingerprint sensor: the screen turns on and unlocks with the press of one button in any case. Why is there no requirement in Compatibility Definition to disable Smart Lock when the fingerprint sensor is active? Mystery. But you can use this system to unlock your device. Just keep in mind that Smart Lock will not be active immediately after you reboot the device; To activate the system, the device will need to be unlocked with a password or pattern at least once.
Our Chinese friends
What about the numerous Chinese phones that also come with fingerprint sensors? Everything is very different there.
Above we talked about Google's requirements as outlined in the Android Compatibility Document. If a manufacturer wants to certify their devices to install Google services on them, their device running a specific firmware version must be certified by one of the laboratories.
In China, Google is banned, and many semi-basement manufacturers are not going to bother with unnecessary certifications. Yes, you yourself know what firmware devices from China often come with. For the sake of performance, encryption, as a rule, is not enabled even in firmware based on Android 6.0, and the bootloader is not fundamentally blocked (in the case of MediaTek processors) or can be easily unlocked. Accordingly, whether there is a fingerprint sensor there or not does not play the slightest role.
Even if encryption is enabled by the user (unlikely in the case of cheap devices, but still), the user has no guarantee that the fingerprint sensor is integrated in the correct way. This is especially true for devices that were sold with Android 5 and earlier versions on board, and received an update to version 6 of Android later.
There are exceptions to this rule. All international models from Huawei and Lenovo are mandatory certified by Google (but this cannot be said about specifically Chinese models). The situation with LeEco smartphones, which are sold in China and are trying to conquer foreign markets, is interesting. In the case of LeEco, for the same model there are often both purely Chinese and international firmware. They differ not only in the pre-installed Google Play store, the list of available languages and the presence/absence of “Chinese garbage”. In the case of international firmware (India, USA, Russia), the company formally certifies the device to install Google Play Services.
In particular, in international LeEco firmware based on Android 6.0 (for example, for Le2 Max), encryption of the data section is activated (and not disabled) - in full compliance with the requirements of the Android Compatibility Document. Many users perceive this as an inconvenience, and they try to switch from such firmware to something else based on Chinese assemblies, which, in light of the unlocked bootloader, completely devalues the entire security model.
How to hack a fingerprint scanner.
Hacking the fingerprint sensor for Android involves imitating a finger with which you can unlock your smartphone. How detailed and high-quality the simulation should be, and what material it is made of, depends on the technology on which the sensor of a particular smartphone model is built.
Thus, it is useless to try to deceive ultrasonic sensors using a fingerprint printed with high resolution on special conductive paper, but standard capacitive scanners can be outwitted in this way.
But the ultrasonic sensor is deceived using a finger printed on a 3D printer, and the material does not really matter. Finally, almost any sensor will mistake for a real fingerprint, made of a thin layer of conductive material and placed over a finger.
There is probably no need to mention that to unlock a phone equipped with a fingerprint sensor, you can use the finger of a sleeping, unconscious person, or even a corpse (the police use this method all the time).
But it is necessary to mention that in some countries governments collect databases of fingerprints of their own and other citizens (ever received an American visa?). And if now legal restrictions do not allow the use of these databases to unlock phones simply on suspicion, then in the future I will not give such a guarantee.
Comparison with Touch ID
It is impossible to directly compare the security of Apple Touch ID with the situation in the Android world: while Apple has only a few devices, there are, on the contrary, too many Android smartphones. They can use a wide variety of sensors based on a variety of technologies (from capacitive and optical to ultrasonic). Different bypass technologies are selected for different sensors. For example, for the Samsung Galaxy S6, the trick of unlocking the phone with a finger model printed on a 3D printer from the most ordinary plastic works quite well (with Apple Touch ID such a simple trick will not work; for printing you will need to use a material with special properties). Some other devices are easily fooled by high-resolution printed images.
But the comparison with Nexus Imprint makes sense. With the Nexus 5X and 6P, Google took an exemplary approach to security. This includes unbreakable encryption of the data section, and competent integration of fingerprint sensors, and the sensors themselves were not chosen anyhow.
Third-party devices may use insufficiently secure sensors and may have obvious security holes (despite formal compliance with the Android Compatibility Definition requirements).
How to protect yourself from fingerprint scanner hacking
Have you read the article and firmly decided to disable the ill-fated sensor in your device, using a complex alphanumeric password instead? Do not rush. It's actually not that bad. In the case of relatively modern Apple devices (starting with the iPhone 6, iPad mini 4, iPad Air), you are not in danger of hacking the fingerprint sensor: even if your fingerprint is scanned in a high enough resolution, the attacker will have absolutely no time to use it A little. Law enforcement can force you to unlock your phone with a fingerprint (and unlike unlocking with a password, they have every right to do this), but to do this they will need to obtain a special warrant that will specify the entire procedure. Receiving a warrant takes time, during which the fingerprint data on your iPhone will have time to “rotate.”
But if you have an Android smartphone... Turn on encryption. Without it, the data from your phone will be lost without any sensors. Disable Smart Lock - it's a gaping security hole. Make sure your device is certified by Google and runs Android 6.0 or later. If this is not the case, I would disconnect the sensor out of harm's way. Finally, take the time to look for information about whether your device’s fingerprint sensor has been hacked and, if so, whether it’s easy or difficult to do. Make a decision depending on how comfortable you are with the difficulty of hacking the fingerprint sensor on your device by a potential attacker.
How to unlock Huawei Honor 20
Usually, after entering the key incorrectly, information about locking appears on the phone display. You will be offered several solutions: the SOS function (needed to call emergency services) and a tool to restore access.
Unlock Huawei Honor 20 via Google Account
If a Google account was linked to your phone, restoring access will be easy. In this case, the smartphone must be connected to the Internet.
- enter incorrect data 5 times - click “forgotten password” at the bottom of the screen - log into your Google account using your email address - a settings wizard will open in which you need to change the data to unlock the screen